
Uncovering the Alarming Surge in Malware Threats in April
May 9, 2023
April was quite an interesting month and brought us a lot of new insights. In addition to the malware threats mentioned in our previous post, we want to bring your attention to the following old and well-known malware families:
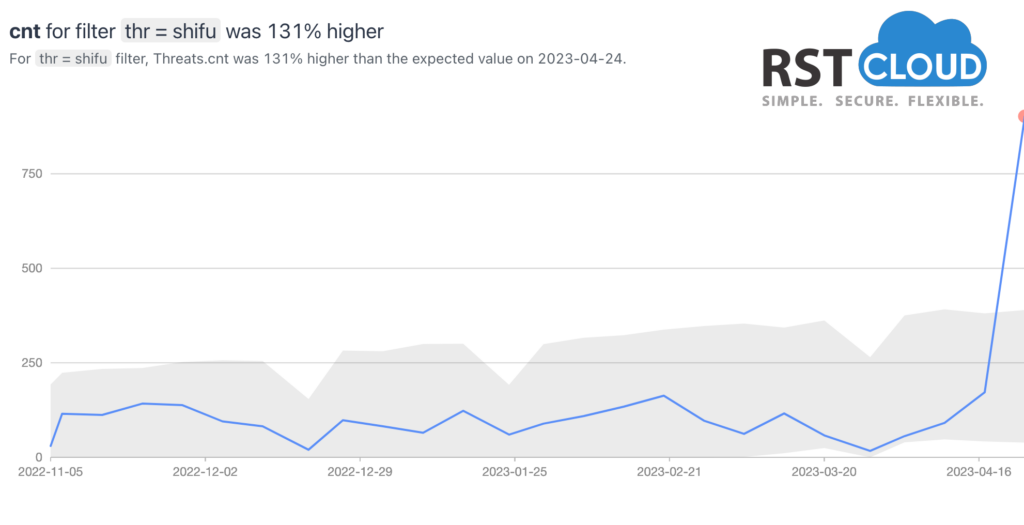
- Shifu,
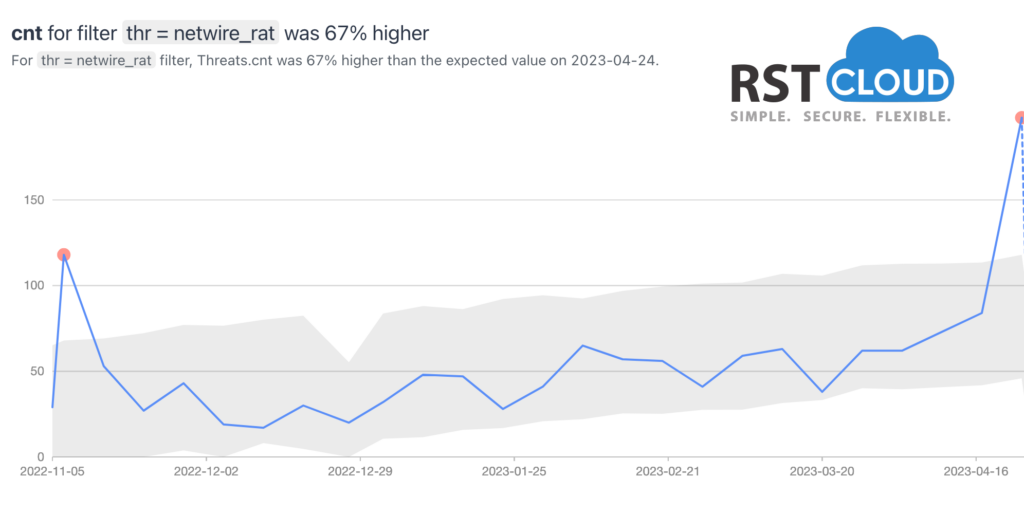
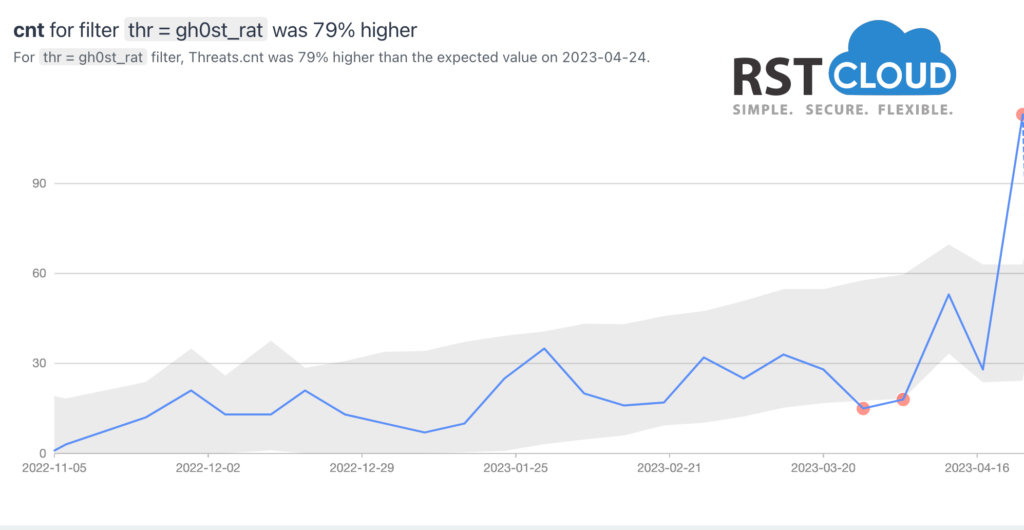
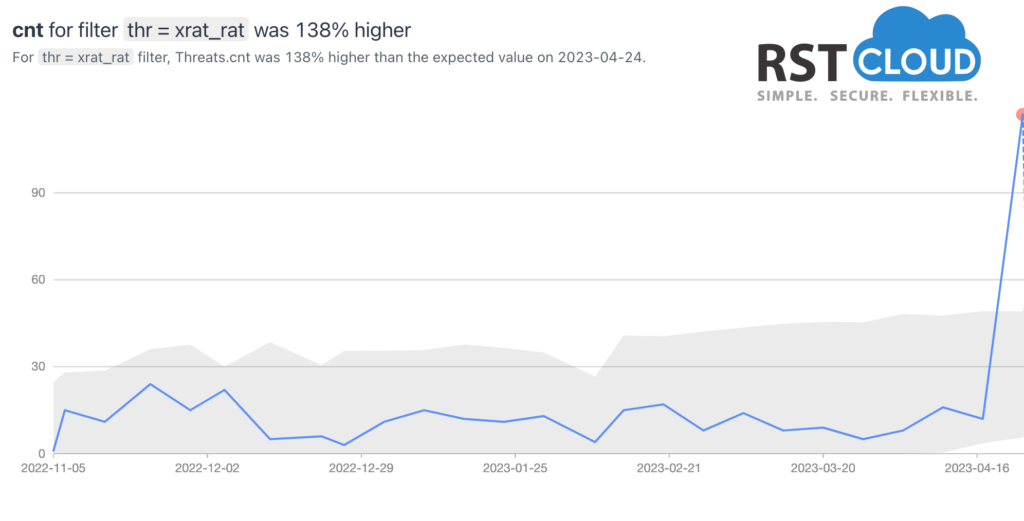
- NetWire, Gh0st, and Xrat RAT,
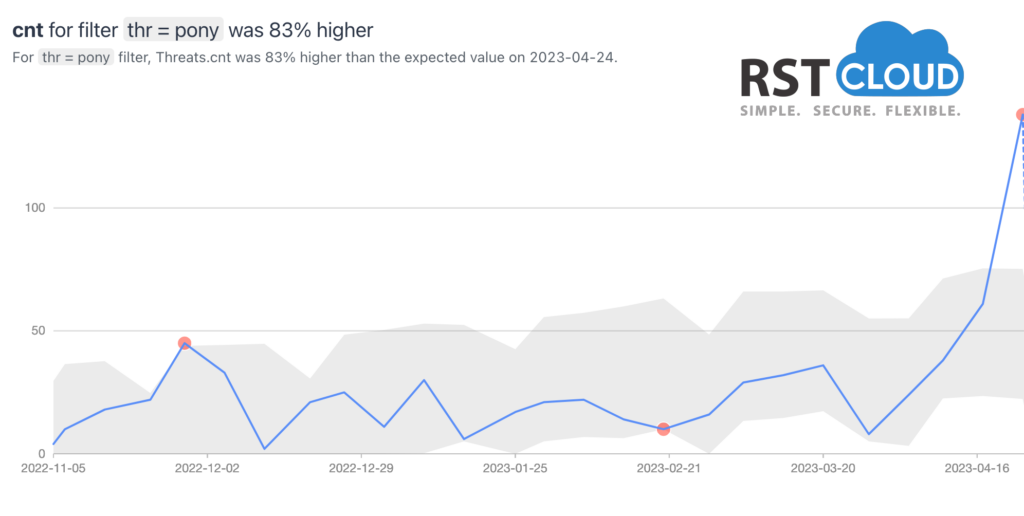
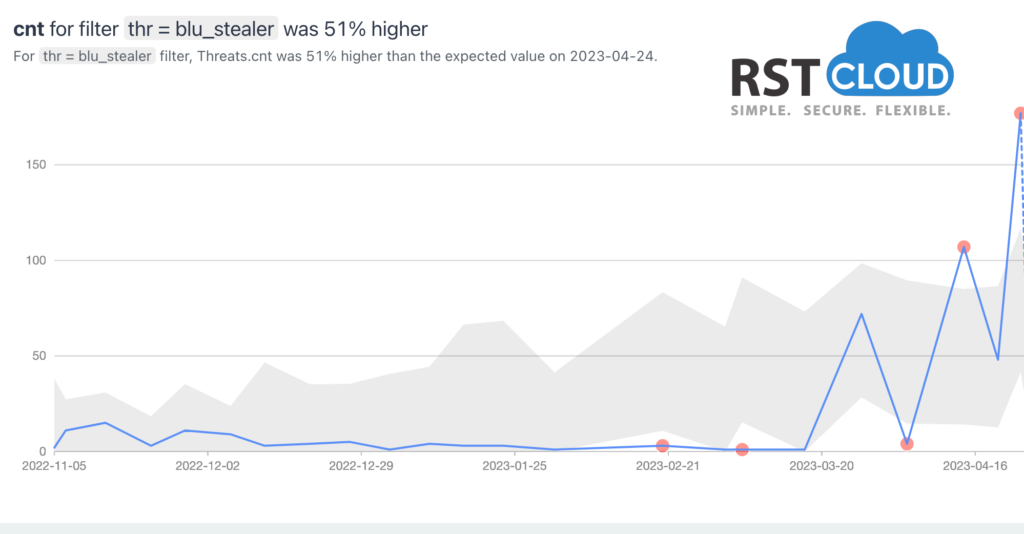
- Pony and BluStealer
These threats could be posing increased risks as we see a rise of indicators related to them found by researchers worldwide. We suggest to give more attention to these threats and assess their potential impacts on you as individuals and organizations.
Shifu is a banking Trojan that was first identified in 2015. It targeted financial institutions and aimed to steal sensitive banking credentials and personal information from victims. While it gained significant attention during its initial wave, it gradually declined in prominence as security measures improved and its operators faced legal actions. Now we see a lot of sandbox reports related to it coming alongside more widespread variants:
- C2/Simda-A
- Mal/Emogen-Y
Despite its age, the emergence of these IoCs suggests that the Shifu malware has resurfaced or evolved in some manner.
xRAT is a RAT (Remote Access Trojan) designed for Microsoft Windows operating systems, which is available as an open-source tool. Although xRAT can serve legitimate purposes, such as enabling a helpdesk technician from an organization to access an employee’s laptop remotely, it has come to the attention of the cybersecurity experts that advanced persistent threat (APT) actors are utilizing xRAT for cyber espionage and criminal campaigns.
NetWire is a RAT that focuses on stealing passwords and keylogging, as well as offering remote control capabilities. This threat has been employed by malicious groups since 2012 and has been distributed through various social engineering campaigns, including malspam. In recent times, NetWire has been distributed as a second payload via GuLoader phishing waves using Microsoft Word documents. This multi-platform malware has undergone several upgrades and has been identified in different types of attacks, ranging from Nigerian scammers and COVID-19 themed spam attacks to APT attacks.
Similarly, Gh0st is a powerful RAT, with its source code dating back to 2001, but it remains relevant and dangerous today. It is utilized on Windows platforms and has been used to hack into some of the most sensitive computer networks worldwide. Gh0st RAT has the ability to take full control of the remote screen on the infected bot, provide real-time and offline keystroke logging, offer a live feed of the webcam and microphone of the infected host, download remote binaries on the infected remote host, and much more.
Pony Stealer is a dangerous password-stealing malware that can decrypt or unlock passwords for lots of applications, including VPN, FTP, email, instant messaging, and web browsers, among others. Once a PC is infected with Pony Stealer, it converts the device into a botnet, allowing it to propagate and infect other PCs.
Although Pony Stealer, also known as Pony Loader and FareIT, among other names, has been in existence since 2011, it remains a significant threat in the realm of credential theft. The malware has been linked to numerous high-profile attacks and countless other thefts, including the theft of almost two million credential sets.
BluStealer is quite a new recombinated information-stealing malware that includes elements of other malicious software such as SpyEx, ThunderFox, ChromeRecovery, StormKitty, and FirePwd. This malware has the ability to extract sensitive information like login credentials, credit card details, and cryptocurrency data. The stolen data is transmitted back to the attacker via SMTP and the Telegram Bot API.
The malware comprises a loader developed in Visual Basic, the payloads carried by the loader vary from sample to sample, indicating that the malware authors are able to customize each component separately.
Staying up-to-date with the latest threats is just as important as implementing essential security measures, such as performing software updates, applying vulnerability patches, utilizing various data and network protection tools, establishing a Security Operations Center (SOC), and promoting awareness. This is why our experts share their knowledge of current threats through various analytical materials and our products.
PS: Why did Master Shifu hire a threat intelligence analyst? – To keep his “Kung-Fu” secure!